This is the procedure I used to root my device running this firmware version. It’s possible the newer versions of firmware will not be rootable via this method. [Settings] -> [About Phone]
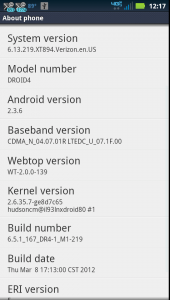
Droid4 About phone dialog
I found the code used for the privilege escalation in this androidevolved.com forum post.
Start by enabling USB debugging on the phone under the menu [Settings] -> [Applications] -> [Development] check USB debugging.
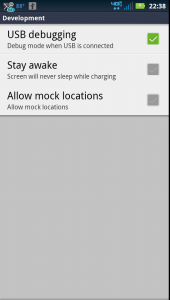
Droid4 Development menu
Connect the phone to the host via a USB port. You should see a new device show up in the kernel dmesg similar to the following and perhaps additional messages if the phone is set to act as a USB mass storage device.
usb 2-4: new high speed USB device number 8 using ehci_hcd
The phone should also notify you of the connection and allow you to open the “USB Connection” manager. It doesn’t matter which connection mode the phone is in as they will all work with adb.
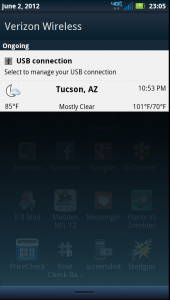
Droid4 USB connection notice
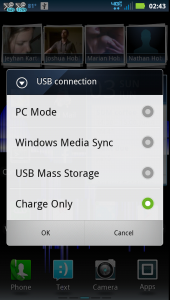
Droid4 USB connection mode dialog
Download and unzip Dan Rosenberg’s “motofail” Droid4 root exploit code. Here is a direct link to the Linux .zip file for the lazy.
jhoblitt@dull ~ $ mkdir droid4
jhoblitt@dull ~ $ cd droid4
jhoblitt@dull ~/droid4 $ wget http://vulnfactory.org/public/motofail_linux_osx.zip
--2012-06-03 02:53:23-- http://vulnfactory.org/public/motofail_linux_osx.zip
Resolving vulnfactory.org... 199.188.204.9
Connecting to vulnfactory.org|199.188.204.9|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1763681 (1.7M) [application/zip]
Saving to: `motofail_linux_osx.zip'
100%[======================================>] 1,763,681 1.79M/s in 0.9s
2012-06-03 02:53:24 (1.79 MB/s) - `motofail_linux_osx.zip' saved [1763681/1763681]
jhoblitt@dull ~/droid4 $ unzip motofail_linux_osx.zip
Archive: motofail_linux_osx.zip
creating: motofail_linux_osx/
inflating: motofail_linux_osx/su
inflating: motofail_linux_osx/run.sh
inflating: motofail_linux_osx/adb.osx
inflating: motofail_linux_osx/motofail
inflating: motofail_linux_osx/adb.linux
inflating: motofail_linux_osx/busybox
inflating: motofail_linux_osx/Superuser.apk
Test that adb is working at all while your phone is attached by running it with the devices command to list any connected Android devices.
If you see this, it means that the phone is not connected via USB or the kernel/UDEV did not detect and/or properly configure a newly connected USB device. Recheck your USB cabling and make sure that the phone is visible in the kernel dmesg and via lsusb.
jhoblitt@dull ~/droid4/motofail_linux_osx $ ./adb.linux devices
List of devices attached
If you see this, it means that the phone is visible as USB device but that adb doesn’t have the proper permissions to access it. This is the expect out of box behavior for most Linux distributions including Gentoo.
jhoblitt@dull ~/droid4/motofail_linux_osx $ ./adb.linux devices
List of devices attached
???????????? no permissions
Now we need to fix the device permission the UDEV is setting up for the phone as a USB device. Find the USB vendor ID / product ID for the phone. All Droid4 / XT894s should be the same as my phone. The product ID will change depending on what USB connection mode the phone is set too. In this example the vendor ID is 22b8, which should be the same for all Motorola devices, and the product ID is 4331, which should be unique to the droid4.
jhoblitt@dull ~ $ lsusb
Bus 001 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
Bus 002 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
Bus 003 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
Bus 004 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
Bus 005 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
Bus 006 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
Bus 007 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
Bus 008 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
Bus 003 Device 007: ID 046d:c52b Logitech, Inc. Unifying Receiver
Bus 004 Device 003: ID 046d:c318 Logitech, Inc. Illuminated Keyboard
Bus 002 Device 007: ID 22b8:4331 Motorola PCS
I got an example udev rule from the cyanogenmod wiki and modified it to cover all of the droid4’s connection modes. I have since added a entry for the droid 4 to the cyanogegnmod wiki. The command below will not work under sudo so run it from a root shell.
# cat > /etc/udev/rules.d/51-android.rules << END
SUBSYSTEMS=="usb", ATTRS{idVendor}=="22b8", ATTRS{idProduct}=="4331", MODE="0660", OWNER="jhoblitt" # PC Mode
SUBSYSTEMS=="usb", ATTRS{idVendor}=="22b8", ATTRS{idProduct}=="4333", MODE="0660", OWNER="jhoblitt" # USB Mass Storage
SUBSYSTEMS=="usb", ATTRS{idVendor}=="22b8", ATTRS{idProduct}=="4335", MODE="0660", OWNER="jhoblitt" # Charge Only
SUBSYSTEMS=="usb", ATTRS{idVendor}=="22b8", ATTRS{idProduct}=="4337", MODE="0660", OWNER="jhoblitt" # Windows Media Sync
END
Disconnect / reconnect the phone to USB to trigger a udev event. adb should now be able to detect the phone.
jhoblitt@dull ~/droid4/motofail_linux_osx $ ./adb.linux devices
List of devices attached
014FD7880F00700A device
We’re now ready to run the root exploit code via the run.sh script in the motofail_linux_osx package. Ignore the line 22 shell script error, it doesn’t need to be fixed.
jhoblitt@dull ~/droid4/motofail_linux_osx $ ./run.sh
./run.sh: line 22: [: too many arguments
[*]
[*] Motofail: Universal Motorola Gingerbread Root Exploit (Linux version)
[*] by Dan Rosenberg (@djrbliss)
[*]
[*] Tested on Droid 3, Droid Bionic, Droid RAZR, and Droid 4
[*]
[*] Before continuing, ensure USB debugging is enabled and that your phone
[*] is connected via USB.
[*]
[*] Press enter to root your phone...
[*]
[*] Waiting for device...
[*] Device found.
[*] Deploying payload...
3576 KB/s (501292 bytes in 0.136s)
[*] Owning phone...
[*] Motofail: Universal Motorola Android Root Exploit
[*] Copyright (c) 2012 Dan Rosenberg (@djrbliss)
[*] Exploit complete.
[*] Rebooting device...
[*] Waiting for phone to reboot.
[*] Attemping persistence...
remount succeeded
357 KB/s (22364 bytes in 0.061s)
3542 KB/s (1867568 bytes in 0.514s)
4438 KB/s (843503 bytes in 0.185s)
[*] Cleaning up...
[*] Motofail: Universal Motorola Android Root Exploit
[*] Copyright (c) 2012 Dan Rosenberg (@djrbliss)
[*] Exploit complete.
[*] Rebooting...
[*] Exploit complete!
[*] Press any key to exit.
And you should now be able to grand applications root privileges on your phone. One easy way to verify that the “rooting” worked is to install the Root Checker app from the Google Play marketplace.
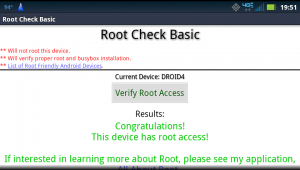
Root Checker app





